
Why Secure Data Sharing Is a Key Business Strategy in 2025
In the modern digital business world, companies are increasingly depending on data to make decisions, improve customers’ experiences and stay competitive. But as reliance on

In the modern digital business world, companies are increasingly depending on data to make decisions, improve customers’ experiences and stay competitive. But as reliance on

The online world has become an indispensable component of our existence, fueling the whole thing from interaction and trade to vital infrastructure. But all that interconnection

Network infrastructure transports communications necessary for applications, services and data. From routers and servers to storage and domain name systems, the components of every network

In a period where electronic learning has transformed into the norm, the security of online educational stages has emerged as a fundamental concern. Institutions are

Professionals have more duties than just advertising in the rapidly evolving digital space, where knowledge is king. These stewards, entrusted with maintaining brand integrity and

As a business owner, there’s a lot to consider and after investing your time, funds, and reputation to build your business, the last thing you
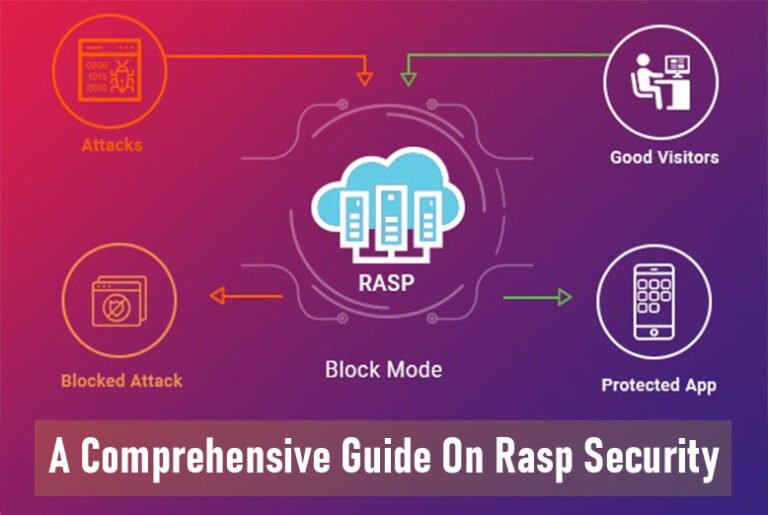
Rasp Pi, a compact and cost-effective micro-computer, has revolutionized computing in education, home automation, and even small-scale industrial projects. However, like any connected device, it’s

Cybersecurity companies are more crucial than ever. The reasons are known to every individual. For the “digital safety.”The frequency and complexity of cyberattacks have escalated

In today’s technologically advanced world, networking plays a pivotal role in ensuring seamless communication and data exchange. Among the array of network infrastructure solutions available,

Cyber attacks can damage a company’s reputation, disrupt operations, and result in financial losses. Like many other countries, Australia faces a significant and evolving cyber

The General Data Protection Regulation (GDPR), which comes into effect on May 25th, 2018, is one of the biggest changes in data privacy regulation for

From issuing admission to an educational institute to opening a bank account, every procedure is marked incomplete in India without the submission of the Aadhaar
Unlock exclusive business insights, emerging trends, and key updates from the Asia-Pacific, delivered directly to your inbox.
For decades, the West led global business. Now, Asia-Pacific is rising, fueled by its economic dynamism. Business APAC tracks this shift, bringing you insights into APAC’s growth in business and technology
Copyright © 2025 – Business APAC. All Right Reserved.