Data Security for Marketers: Safeguarding Digital Assets
Professionals have more duties than just advertising in the rapidly evolving digital space, where knowledge is king. These stewards, entrusted with maintaining brand integrity and fostering customer relationships, are in ...
Read More →
Why Your Business Needs a Commercial Alarm System
As a business owner, there’s a lot to consider and after investing your time, funds, and reputation to build your business, the last thing you want is for its security ...
Read More →
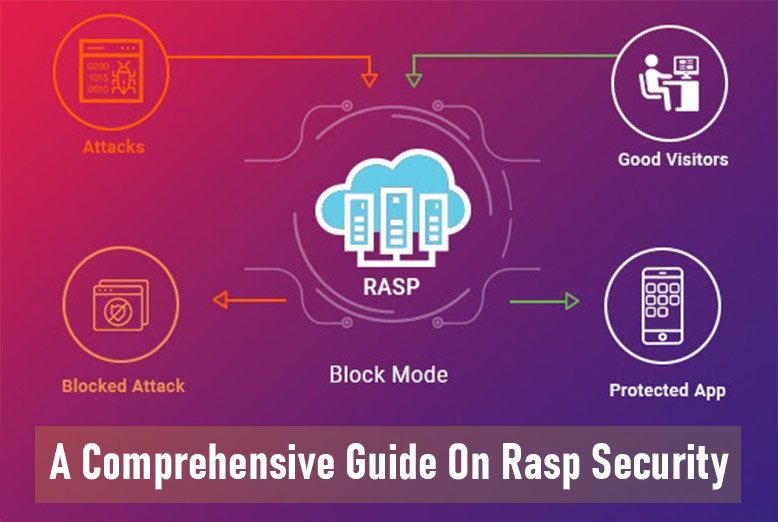
A Comprehensive Guide On Rasp Security
Rasp Pi, a compact and cost-effective micro-computer, has revolutionized computing in education, home automation, and even small-scale industrial projects. However, like any connected device, it’s susceptible to security threats. In ...
Read More →
Top 10 Cybersecurity Companies in India (Updated 2023)
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. Most cyberattacks aim to access, alter, or destroy confidential data, extort money from users through the use ...
Read More →
What is F5 Networks used for?
In today’s technologically advanced world, networking plays a pivotal role in ensuring seamless communication and data exchange. Among the array of network infrastructure solutions available, F5 Networks has emerged as ...
Read More →
Aligning Your Cyber Security Strategy with Industry Standards and Regulations
Cyber attacks can damage a company’s reputation, disrupt operations, and result in financial losses. Like many other countries, Australia faces a significant and evolving cyber threat landscape. The reliance on ...
Read More →
What You Need to Know About GDPR & email verification
The General Data Protection Regulation (GDPR), which comes into effect on May 25th, 2018, is one of the biggest changes in data privacy regulation for over 20 years. It’s clear ...
Read More →
Masked Aadhaar Card ID: Is it Enough Secure to Prevent Frauds and Misuse?
From issuing admission to an educational institute to opening a bank account, every procedure is marked incomplete in India without the submission of the Aadhaar Card. It is a vital ...
Read More →
16 Tips For Protecting Confidential Business Information
Companies should go to great lengths to protect sensitive information from competitors, the public, and team members that could potentially misuse the data. With technology advancing at an alarming rate, ...
Read More →
The Undoubted Tale of Chinese Apps and Security Breaches
In a piece of latest news, the Indian government (once again) banned 54 Chinese apps in a row. Citing security concerns, the ban is a result of tensions between India ...
Read More →
How to reduce Fuel Theft with Innovative Technology?
Fuel theft is one of the major problems faced by Australia. This crime has been escalating since the pandemic. The fact that the petrol price has risen significantly is considered ...
Read More →
Australia and South Korea agree to a $717 million defense contract
Key Highlights: Australia’s Prime Minister Scott Morrison and South Korean President Moon Jae-in have agreed to a $717 million defense contract. Australia recently signed a pact with the United States ...
Read More →